This essay follows on from another of my programming challenges.
The first one looked at some of the elements of the Lorenz system for encryption, which was important during World War Two.
If you want to send a message by radio, you have a problem: Anyone can eavesdrop in the transmission. The first programming challenge showed how the characters of a message can be turned into a string of 1's and 0's. Once you have the 1's and 0's, you can do things with them to frustrate eavesdroppers.
The first challenge described a process you could apply to the 1's and 0's to make them seem like gibberish to anyone not aware of the process.
It would not stop a real-world enemy decrypting the message, but it illustrated elements of such systems.
This programming challenge derives from what was actually done to the 1's and 0's to scramble them. And it invites you to try to write programs to accomplish the same things and/ or to create virtual equivalents of things that were done electro-mechanically in World War Two, before transistors made it easy to do them electronically.
Why bother?...
Do mountain climbers worry about why they do what they do? We program because the challenge is there, don't we?
And also, if you try to build one of these in software, it might give you a sense of wonder and admiration for the people who made the original electro-mechanical version.
You don't need it to enjoy this programming challenge, but if you want to understand the Lorenz encryption more fully, the discussion at a page on codesandciphers.org.uk is excellent. It includes the diagram below of the core mechanical elements of the Lorenz machine...
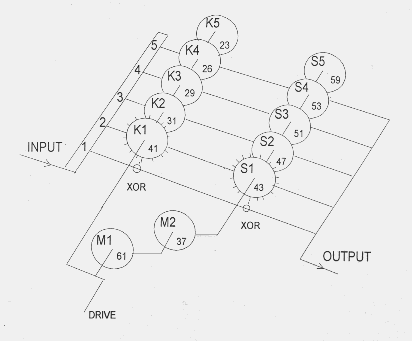
You'll need to know what "XOR two bits" means. (In this context, a "bit" is a one or a zero. I've tried to use "bit" only thus throughout these two pages of programmking challenges. (Help the next reader? Tell me of any lapses? Contact details at bottom of page.)
Suppose I had 3 marbles in my left hand and 2 in my right hand, and put them all in a cup. If I ask how many marbles are in the cup, you can say 5, can't you? You can do "ADD two numbers".
"XOR two bits" is easier. If you have two bits, you have one of the following...
0 and 0 or 0 and 1 or 1 and 0 or 1 and 1
"XORing" is just a mathematical thing. Like the adding that got 5 from 2 and 3.
If you "XOR the two bits", you work out a result.
If the two bits are the SAME (0/0 or 1/1), then the result is 0.
Otherwise the result is 1.
The word, XOR, comes from eXclusive OR. If one OR the other of the bits is a 1, then the result is 1... eXcluding the case where they are BOTH 1.
WHO CARES!
Before I answer that, let me tell you one other thing about XOR...
If someone says "XOR 1110 and 0110", you line them up, like this...
1110
0110 ... and do each column of bits by the XOR rule, leading to...
1110
0110
====
1000
1110 XOR 0110 is 1000. (This is sometimes called "doing a bitwise XOR".)
So now you know!
"Roll with me baby", as the wonderful Ms Parton says in the song.
Alice wants to send 01010101 to Bob. (I showed in the first challenge in this group how ordinary, human-friendly, text can be turned into strings of 1's and 0's.)
Alice and Bob, by prior arrangement, both know that the key they are going to use for this message is 11110001. (This is the first 8 bits of a much longer key they pre-shared. We only need the first 8 bits for this message from Alice because it is only 8 bits long.)
Alice XOR's her message with the key...
01010101
11110001
========
10100100
Alice sends Bob the result of the XOR (10100100). (It's the "encrypted text".)
Bob then XOR's the encrypted text with the key....
10100100
11110001
========
01010101 .... and Hey Presto Hurrah!... the gibberish from Alice has been turned back into the message she wanted Bob to see.
And the "encrypt, send, decrypt" system is built around a nice, simple little rule!
The only snag is that they need a good key. And they have to pre-share the key.
Or do they?
What if they both had a machine which would GENERATE a long string of 1's and 0's to use for the key? And it would generate different keys if you simply changed some settings on the machine before you started it churning out the 1's and 0's? But always generate the same string of 1's and 0's for any given settings on the machine?
You still have to pre-share what settings you are going to use. You won't want use the same settings for every message. Perhaps you change the settings each day at midnight? Some system like that would need to be agreed between Alice and Bob.
Alice and Bob are ready to exchange messages securely once they have their key-making machines and their plan for the settings for them.
THAT was how the Lorenz encryption system worked! Of course, the machinery helped you with parts of the XORing, etc, etc. But the basis of how it worked are as above.
There's more about this sort of thing in the Wikipedia article about the Vernam cipher.
You can read an alternative explanation the Lorenz system at Wikipedia. Perhaps read it at some point, and see if what you've grasped from this matches what you find there? (Help the next reader of my challenge? Let me know if I've led you astray anywhere? Contact details at bottom.)
Try to write a program which will take some text, accept some settings, and then encrypt that text as above.
At the same time... without using the obvious cheat... it should take the encrypted version, and turn it back into the original plaintext.
Your key generating algorithm doesn't have to be brilliantly clever. For this part of the challenge, it doesn't have to produce a GOOD key. (In a GOOD key, there would be no pattern to the 1's and 0's.)
It could be something as simple as a key generator set by supplying two numbers. If you gave it 3 and 2, the key generator would give you 00011000110001100011....
You should put the key generator into two sub-routines. Call them SupplyWordOfKey-First and SupplyWordOfKey-Later, so that it is easy read your code alongside the code from other challenge participants. (The first sets the generator up, and delivers the first bit. The second supplies another bit each time it is called.)
SupplyWordOfKey-Later would need to have access to "how far we've got". I'm not a very good programmer, and would probably involve too many global variables in my implementation. But if you don't mind doing that, the task isn't very difficult.
First try to understand how the key used in the Lorenz machine was generated. The explanation I mentioned earlier at codesandciphers.org.uk would be a great place to start.
Then try to adapt the answer you came up with for the challenge above. Make it use keys that the Lorenz mechanism would have created. It will, of course, be necessary to provide ways to set up your "virtual Lorenz" in the ways the Lorenz mechanism was set up.
You don't need to incorporate everything that was in the original. Incorporate as much as you can, or as much as amuses you.
If you do this, and, while you're doing it, think about the engineers who made the original Lorenz, without transistors, you may feel some awe and wonder.
I hope you do try the challenge. I hope you feel the awe and wonder.
Remember: All we've been doing here is looking at how things were done with Lorenz machines by people who had the right to use them, and knew what settings the person they were communicating with were using.
We haven't looked at trying to decrypt an intercepted bit of encrypted text.
The people at Bletchley Park managed that too. Without transistors.
Please get in touch if you discover flaws in this page. Please mention the page's URL. (wywtk.com/ardu/lor/lorenz1a2.htm).
If you found this of interest, please mention in forums, give it a Facebook "like", Google "Plus", or whatever. If you want more of this stuff, help!? There's not much point in me writing these things, if no one feels they are of any use.
|
Unlike the clever Google search engine, this one merely looks for the words you type, so....
* Spell them properly.
* Don't bother with "How do I get rich?" That will merely return pages with "how", "do", "I"....
Please also note that I have three other sites, and that this search will not include them. They have their own search buttons.
http://www.arunet.co.uk/tkboyd/index2.htm My site at Arunet. (Not httpS- sorry!)
![]() Page has been tested for compliance with INDUSTRY (not MS-only) standards, using the free, publicly accessible validator at validator.w3.org. It passes in some important ways, but may still need work to fully meet HTML 5 expectations.
Page has been tested for compliance with INDUSTRY (not MS-only) standards, using the free, publicly accessible validator at validator.w3.org. It passes in some important ways, but may still need work to fully meet HTML 5 expectations.
....... P a g e . . . E n d s .....