
Are you studying programming, or doing it for the fun of it?
Then I hope will enjoy this page.
Fear not! I'm not just saying "Why not write a program to simulate the World War II Enigma machine?" Maybe you will achieve that eventually... but it is a pretty big ask. The challenge comes in parts. Can you at least create a program which simulates an encryption device with only a stecker board? (Stecker boards explained below.)
The prime objective of this page is not that ultimate goal. The prime objective is to present some ideas for creating simulations of parts of the Enigma machine. I believe that even intermediate programmers will be able to have some success. How far will you get?
I also hope you'll be inspired to learn more about the machine, it's place in history, the breathtaking achievements... and sheer work... of the people at Bletchley Park.
The machine was a small box... only a bit bigger than an old fashioned portable typewriter. I was mostly a mechanical device, but it did need a simple 4v battery to light up some small bulbs.
It had 26 keys, each marked with a letter of the alphabet. Like a rather limited keyboard for a typewriter or computer. I will call them "buttons" from now on, to reserve the word "key" for something else.
The machine had 26 small glass windows, with a letter painted on each, and a light bulb below it. When I refer to "the bulbs" it is these that I mean.
Let's say you wished to encrypt "START RUNNING". First you made some settings of the machine. Those settings constitute the "key" used for the encryption of your message.
Then you would press the S button. And one bulb would light up, let's say it would be the "X".
You'd make a note of the "X", and carry on...
Button pressed: S T A R T R U N N I N G Bulb that lit up: X W G R G W T F T J S M
"XWGRGWTFTJSM" would be the encrypted form of your message. (Enigma didn't have any way to show a space, or lower case letters.)
(In passing: Note that the two N's in running do not both encrypt to the same letter. There are other examples of this in the sample. They might, sometimes, encrypt to the same letter, but that would be unusual. The job of the eavesdropper was not easy!
Once the recipient had the message ("XWGR..."), he/ she would get their Enigma machine out, put the "key" in (i.e. set the machine to the same settings used for the encryption. And then simply press the buttons and note the bulbs which came on!
Button pressed: X W G R G W T F T J S M Bulb that lit up: S T A R T R U N N I N G
Wonderfully simple to use! It was a very elegant machine.
I've done a page with many more details about how the machine worked. But you won't need them to press on with this page.
I have to ask you to bear with me for a while. The easy path I will take you along may not seem worth the trouble at first. But if you are patient, I hope the later, more complicated, more related to Enigma parts will be more easily understood.
In what follows, I will be pretending that we only want to encrypt 6 letters! (A,B,C,D, E and F). If you understand doing that, extending it to doing 26... or more... letters/ characters is easy. (As long as the number you choose is even!)
A VERY simple "Enigma" could look like this. It would have the rather unfortunate limitation of always "encoding" A as A, B as B, etc.
Remember me asking you to bear with me???

Now... just a little addition... The following is very nearly exactly a part of the Enigma machine. It was called the "stecker board"....
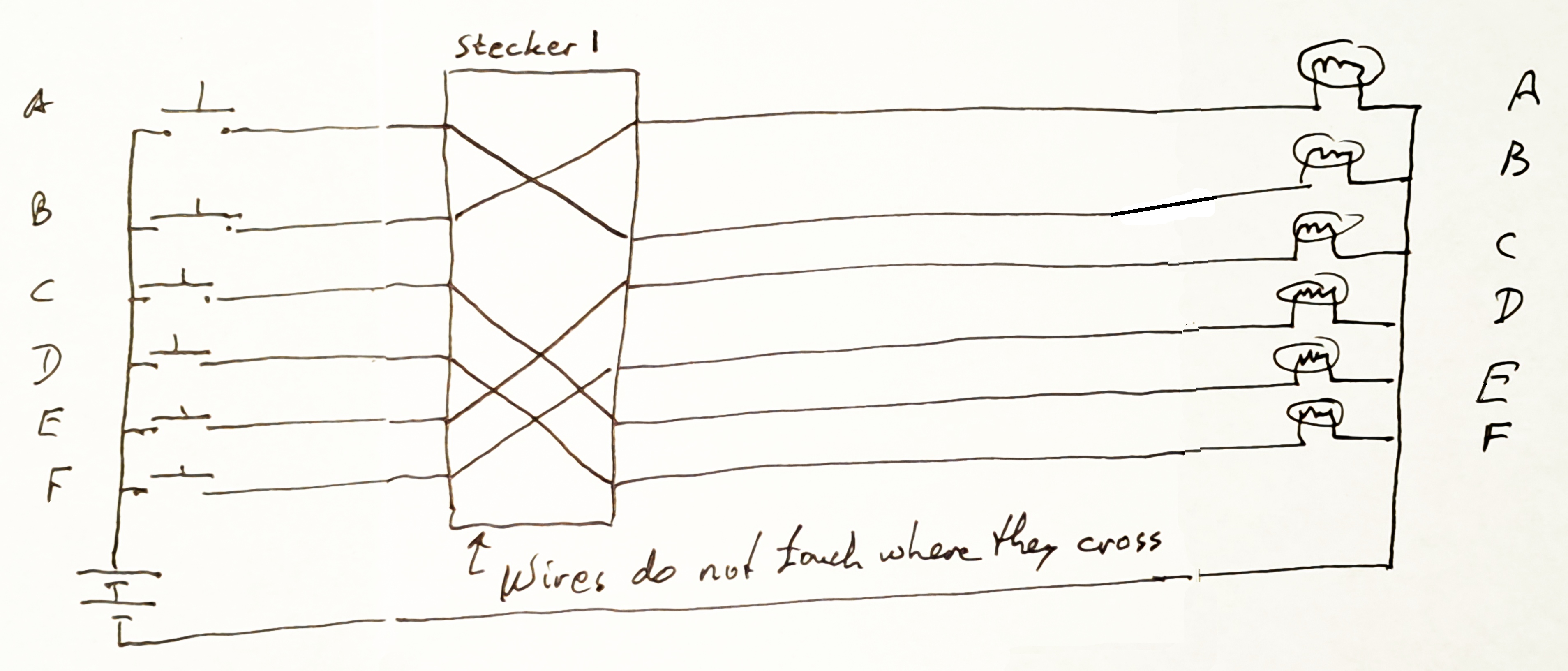
Now, if you pressed the A button, the B button would light. The full table would be...
Button pressed: A B C D E F Bulb that lit up: B A E F C D
In the "real" Enigma machine, the re-routing of wires was accomplished by plugging cables into a board... a bit like an old fashioned telephone switch-board.
If what cable was plugged on where, the paths between buttons and bulbs changed. Our simulator should be able to handle this!
On the original Enigma machine, because of the system of cables and sockets, the only wirings possible swapped two letters. E.g. "A" went to where "B" used to AND "B" went to where "A" used to. More complex swappings could be allowed, if you wished, but I suggest we all stick with trying to closely simulate the original.
The program for our simple "one stecker" simulation could look like the following. If the user was done, entering "9" would end the run.
SetThingsUp Repeat Get a letter from operator. (Put it in variable "Letter") Letter=StekerChange(Letter) Display(Letter) Until Letter=9
SetThingsUp is a procedure where things like getting the current stecker board wiring would be entered into the program.
SteckerChange is a function. It must use a data structure, filled during "SetThingsUp", to determine what "line" the circuit would follow for the letter presented to it. For example, if "C" was in the "Letter" variable when the function was called, then the function would return "E".
START with a SIMPLE simulator, with a "fixed" stecker board. Once you have that working, see if you can give the user a way to say "Today, I want the stecker board to do THESE swaps."
I wrote the rest of this a while ago. On revisiting it, a worry occurred to me.
While I stand by all I have said, I may have inadvertently put a stumbling block in your way by how I expressed some ideas.
The process does indeed start with the input of a letter from the user.
And it ends with a letter being returned to the user.
However, line of pseudo-code that says we want...
Letter=StekerChange(Letter)
... is perhaps going to lead you astray.
While my diagram is only that, a diagram, it may be helpful to think of the "path"(?) from the input to output in those terms.
Let me use the same specific example again (encrypting "C"):
Perhaps "Letter" should hold not the letter, but the letter's position "up" or "down" the column of buttons. And the SteckerChange function should, perhaps, be given the position of the incoming "wire", and return the position of the onward connection?
Display(Letter) would need to be clever enough to turn the position of the wire that reaches back to the C into the letter associated with the bulb at that position in the column of bulbs.
As I write this, I become more and more confident that this is the way forward. Apologies for not re-writing the page just now!
In the simple case where we only have the stecker board introducing a little encryption, it's all a bit academic. When we move on to the more complex elements of the Enigma, it will become more critical.
In the Enigma, what we've done so far was done. But it was only a first step.
The "wires" coming out of the stecker didn't go directly to the bulbs. Instead, they connected to more elements which swapped connections up and down, a bit like the stecker. And (in simple terms) there were three additional scramblings.
BUT. And it is a huge But.
The subsequent connection swappers didn't apply static rules. Their rules for the swaps they would make CHANGED as the process progressed.
To simulate the equivalent with our 6 letter simulation, we'd add three more elements which would be very like the stecker. Except what the wire swaps are in each would change. The first one would change after every letter was processed. The second would change once for every 6 letters processed, and the third would change once for every 36 letters processed.
The new wire swapping rules wouldn't be random. Out of the mechanical answer that was the WW II Enigma, a pattern emerged. Again... in terms of our 6 letter simulator, the first stage of the scrambling might look like...
Letter In // Out1 Out2 Out3 Out4.. and so on... until we get back to Out1 v A // C B D E B // F C B D C // A F C B D // E A F C E // D E A F F // B D E A
This part of the encryption was taken care of by "the rotors".
So, our program can become...
SetThingsUp LetterCount=0 Repeat Get a letter from operator. (Put it in variable "Letter") Letter=StekerChange(Letter) Letter=Rotor1(LetterCount,Letter) Letter=Rotor2(LetterCount,Letter) Letter=Rotor3(LetterCount,Letter) Display(Letter) LetterCount=LetterCount+1 Until Letter=9
"All" you need to do is to come up with the three new functions. (And manage when their swapping rules should change.)
Modular arithmetic will be very useful in this program.
The value in LetterCount will go 0,1,2,3,4,5,6,7,8,9,10,11,12...
But LetterCount MOD 3 on that series would generate 0,1,2,0,1,2,0,1,2,0,1,2,0.
You'd use LetterCount MOD 6 inside Rotor2, and LetterCount MOD 36 inside Rotor3
Does this sketch a PERFECT simulation of an Enigma machine? No, not yet. But if what's been suggested above is achieved, tidying it up to make it fully simulate the real thing would not be terribly difficult.
Good luck! I hope you will give it a try, and I hope you'll have fun with that.
If you found this of interest, please mention it in forums, give it a Facebook "like", or whatever. If you want more of this stuff, help!? There's not much point in me writing these things if no one feels they are of any use, is there? I'm not telepathic. Encouragement will be appreciated! Contact details below.
Search across several of my sites at once with a Google search button.
Or...

Or...
|
Unlike the clever Google search engine, this one merely looks for the words you type, so....
* Spell them properly.
* Don't bother with "How do I get rich?" That will merely return pages with "how", "do", "I"....
Please also note that I have three other sites, and that this search will not include them. They have their own search buttons.
It's both! Flat-Earth-Academy.com is something I started years ago. For a variety of reasons, I can't offer you httpS:// access there. (As you are not asked to input any information, that's moot, but it "worries" search engines.) So I'm moving to my new, all singing, and will do the httpS:// dance site, "WYWTK.com", and Flat-Earth-Academy is gradually acquiring pages there. (Well, HERE, as what you are reading is one of my "wywtk/fea" pages.)
Why "WYWTK"? It comes from "What You Want To Know".
![]() Page has been tested for compliance with INDUSTRY (not MS-only) standards, using the free, publicly accessible validator at validator.w3.org. It passes in some important ways, but still needs work to fully meet HTML 5 expectations. (If your browser hides your history, you may have to put the page's URL into the validator by hand. Check what page the validator looked at before becoming alarmed by a "not found" or "wrong doctype".)
Page has been tested for compliance with INDUSTRY (not MS-only) standards, using the free, publicly accessible validator at validator.w3.org. It passes in some important ways, but still needs work to fully meet HTML 5 expectations. (If your browser hides your history, you may have to put the page's URL into the validator by hand. Check what page the validator looked at before becoming alarmed by a "not found" or "wrong doctype".)
Why does this page cause a script to run? Because I have my web-traffic monitored for me by eXTReMe tracker. They offer a free tracker. If you want to try one, check out their site. Why do I mention the script? Be sure you know all you need to about spyware.
....... P a g e . . . E n d s .....